Cyber Security

Vulnerabillity Assessment
Harden your attack surface
RADAR VULNERABILITY RISK MANAGEMENT
Adversaries Don’t Need Many Vulnerabilities – One Is Enough.
90
Every 90 minutes a new security vulnerability is identified
7
That is an average of 7 vulnerabilities per asset across a typical IT environment
8000
8000 known and disclosed vulnerabilities known and disclosed vulnerabilities each year
50-300
50-300 critical vulnerabilities exploitable depending on industry
103
It takes an average of 103 days until known security vulnerabilities are remediated
15
It takes 15 days in the average that a vulnerability is exploited
Vulnerabilities And Their Exploitation Are Still The Root Cause Of Most Breaches
There are many ways to breach corporate defenses, but web applications are by far the most vulnerable part of your network.
The majority of exploits are based on vulnerabilities already known to security professionals for at least one year.
Only constant scanning and ruthless control can help you find vulnerabilities before anyone does.
Rapidly changing, complex business IT environments lead to a broad attack surface
That’s where Radar comes in
Manage Business-Critical Vulnerabilities
Radar is a turnkey, enterprisegrade vulnerability scanning and management platform.
It combines IT asset discovery and inventory, identification and management both internal and external threats.
Report on risks and conduct compliance to current and future regulations (such as PCI and GDPR compliance).
Radar gives you visibility into shadow IT: map your full attack surface and respond to critical vulnerabilities associated with cyber threats.
Explore beyond your network
Identify risks and potentially vulnerable external connections
Discover network assets
Map all assets on the application layer
Scan systems and applications
Protect endpoints. Scan assets for vulnerabilities
Manage vulnerabilities
Central vulnerability management and security alerting and forensics
Assess and verify
Track all changes with PCI-compliant vulnerability scanning
Report status
Prepare standardized and custom reports on risk and compliance
What Is Your Attack Surface?
The best threat response is to predict and map your cyber security threats. No other technology does that better than vulnerability management.
An organization’s attack surface crosses all network infrastructures, software, and web applications internally and in the global Internet. It includes an understanding of all points of interaction.
Information security managers need to be able to approach vulnerability assessment from several perspectives in order to get an accurate assessment of risks, minimize security threats, and maintain compliance.
Unlike any other vulnerability solution on the market, Radar features web crawling technology, called Internet Asset Discovery, that also covers the deep web. Radar allows you to easily browse through all targets to quickly identify risks and potentially vulnerable connections, and to expand the possible attack surface beyond your own network.
Identify And Expose The Possible Threats
Successful intellectual property and brands often make companies the target for fraudulent or malicious activities.
Radar can generate a threat assessment report of activities including brand violation or phishing sites intended to scam or infect visitors. Radar identifies your organization’s assets where they are vulnerable. You can minimize your attack surface while reducing risk.
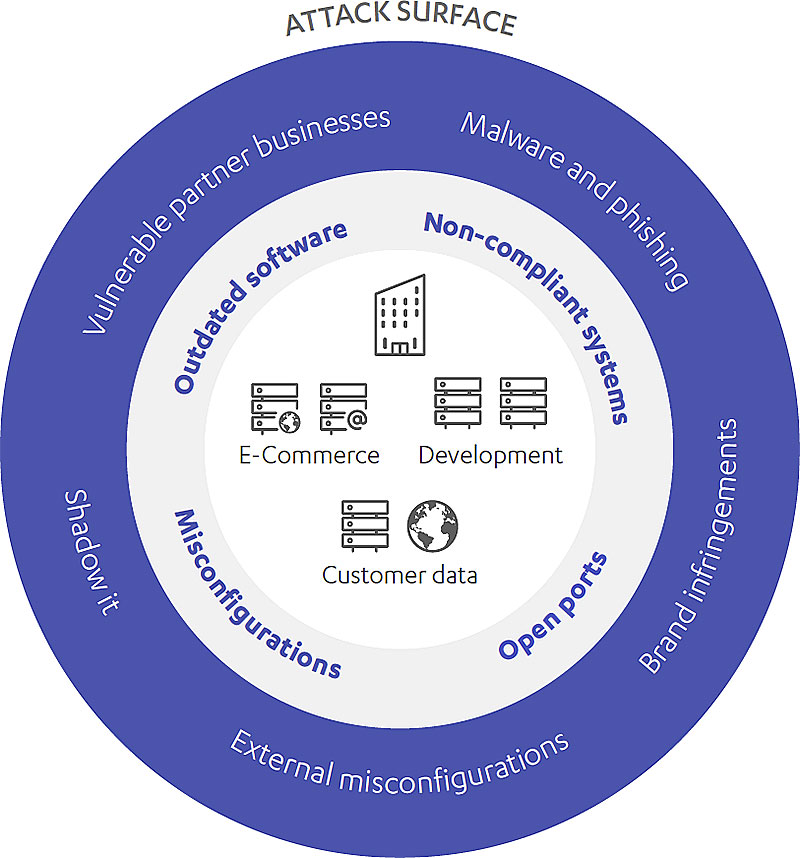
With Radar, your IT security team maps your organisation’s attack surface in the aggregate of:
All known, unknown, and potential vulnerabilities critical to business
Controls across all software, hardware, firmware, and networks
Shadow IT, external misconfigured systems, malware websites, website-linked hosts
Partner and contractor security entropy
Brand infringements and phishing
The Real Attack Surface
BLUE —> What you didn’t want to know you have
GREY —> What you didn’t know you have
WHITE —> What you know you have
Radar Vulnerability Risk Management
Comprehensive visibility
Effective security mapping through precise discovery and mapping of all assets, systems, and applications on the network and beyond.
Streamlined productivity and security management
Quickly address problems across multiple domains with an efficient service workflow, including vulnerability monitoring, automated scheduled scans, and ticketing for prioritized remediation and verification.
Reporting on risk
Produce reports with credible information about your organization’s security posture over time. Show and justify how IT security enables business continuity.
Reduced costs
Vulnerability management can lower the cost of security significantly. It’s less costly to deal with security before serious problems than during a crisis or incident recovery. Additionally, Radar’s cloud resources allow organizations to lower their expenses.
CERTIFICATIONS

